iSCSI Components
For iSCSI communication, the following components talk with each other:
- iSCSI Initiator
- iSCSI Target
iSCSI Initiator
A client in an iSCSI storage network is called the iSCSI Initiator Node (or simply, 'iSCSI Initiator'). This iSCSI Initiator can connect to a server (the iSCSI Target). In doing so, the iSCSI Initiator sends SCSI commands to the iSCSI Target. These SCSI commands are packaged in IP packets for this purpose.
The following forms of iSCSI Initiators are available:
- iSCSI Hardware Initiator: a PCI-X or PCIe card, which implements the iSCSI functionality. Such a card is also called an iSCSI HBA. In the server’s operating system, such an iSCSI HBA appears to be a RAID controller or an FC HBA. With an iSCSI HBA, booting a server through iSCSI is possible. Examples are:
- iSCSI Software Initiator: an iSCSI Initiator implemented by software. The computing operations of the iSCSI initiator are performed by the server’s CPU in this solution (and not by hardware components on a proprietary PCI-X or PCIe card). Thanks to the increased performance of modern server CPUs, this is no longer a problem. Standard network cards are used on the hardware side for communication with the iSCSI Target. Examples of this are:
- Linux Open-iSCSI Initiator
- Microsoft iSCSI Software Initiator
- VMware iSCSI Software Initiator for VMware ESX/ESXi
As long as booting from iSCSI is not a criterion, nothing speaks against the use of iSCSI Software Initiators. With some additional configuration effort, booting from the network with the iSCSI Software Initiator really is possible.[1][2][3] iSCSI Software Initiators are less expensive, widely distributed and very stable. Even iSCSI over 10 Gbit Ethernet will be able to be easily implemented in the future using normal 10 Gbit Ethernet adapter cards.[4]
iSCSI Target
A server in an iSCSI storage network is called the iSCSI Target Node (or simply, 'iSCSI Target'). Such an iSCSI Target can provide one or more so-called logical units (LUs). The abbreviation “LUN” is often used for the term “logical unit” (although this abbreviation actually means “LU Number” or “logical unit number”).
The following forms of iSCSI Targets are available:
- as hardware as iSCSI Storage Arrays (such as EMC AX4-5i or IBM DS3300).
- as Software as iSCSI Target Software for installation on a standard server:
- Linux: LIO Target (linux-iscsi.org), for more targets for Linux, see LIO Features Comparison
- Windows: Microsoft iSCSI Software Target 3.3
iSCSI Server implements the iSCSI Target functionality in various manners:[5]
- Some iSCSI Storage Arrays have precisely one iSCSI Target (the Storage Array itself)
- Other iSCSI Storage Arrays have several iSCSI Targets, such as.
- a iSCSI Target per phys. Interface:
- NetApp
- EMC CLARiiON
- a iSCSI Target per LUN:
- Dell/EqualLogic
- HP/LeftHand
- Any configuration iSCSI Targets desired:
- With EMC Celerra Arrays up to 1,000 iSCSI Targets can be configured and assigned to any virtual or physical network interface desired
- a iSCSI Target per phys. Interface:
SCSI Origins
The origin of iSCSI can be found in the standard SCSI (Small Computer Systems Interface). Considered precisely, iSCSI is the invocation of the SCSI remote procedure model through the TCP protocol:[6]
- 'SCSI commands' are transmitted as 'iSCSI requests'
- 'SCSI responses' and 'SCSI status' messages are transmitted as 'iSCSI responses'
The iSCSI Initiator and the iSCSI Target use for a communication individual messages. Such an iSCSI message is called an 'iSCSI protocol data unit'.
iSCSI Communication
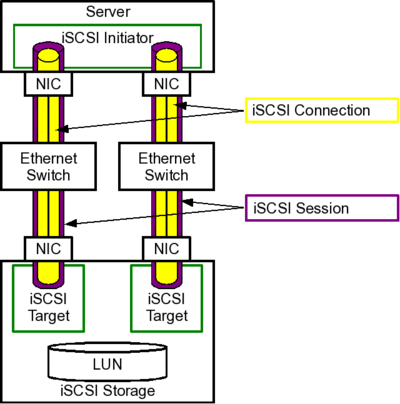
As mentioned above, an iSCSI Initiator and an iSCSI Target talk with each other. The conversation is always started by the iSCSI Initiator. One or moreiSCSI Connections may be used for a conversation (for each iSCSI connection a dedicated TCP connection is used). One such conversation is called an iSCSI Session.
The following image shows the schematic construction of an iSCSI setup:
iSCSI Session Types
Under iSCSI, there are two types of sessions:[7]
- Normal operational session: which involves an unlimited session.
- Discovery-session: this type of session serves only for target discovery. The iSCSI Target may permit SendTargets text requests in such a session.
The type of iSCSI session is defined during iSCSI login.
iSCSI Multipathing
The following types of sessions can be implemented for multipathing under iSCSI:
- using General Storage Multipathing Technologies, which have been settled on top of the iSCSI protocol regardless of the transmission technology
- using iSCSI Multiple Connections per Session (MC/S)
General Storage Multipathing Technologies – so-called Multipath I/O
For storage multipathing that should operate independently of the transmission technology there are two areas:
- Storage multipathing by the operating system (such as the Linux device mapper, MPIO)
- Storage multipathing by software solutions from the storage device manufacturer (such as EMC Powerpath)
The Storage Multipathing Technologies article provides details regarding these options.
iSCSI Multiple Connections per Session (MC/S)
Beyond that, iSCSI also provides options for multipathing over MC/S (Multiple Connections per Session) directly in the protocol. In order to be able to use MC/S, both the iSCSI Initiator and the iSCSI Target must support MC/S.
| Initiator | MC/S Support? | Additional information |
|---|---|---|
| Linux Open-iSCSI Software Initiator | no | ISCSI Multipathing under Linux |
| Microsoft iSCSI Software Initiator | yes | http://technet.microsoft.com/en-us/library/dd759096.aspx |
| Target | MC/S Support? | Additional information |
|---|---|---|
| EMC CLARiiON | no | |
| EMC Celerra | yes | http://technet.microsoft.com/en-us/library/dd759096.aspx |
| NetApp | yes | http://technet.microsoft.com/en-us/library/dd759096.aspx http://blogs.netapp.com/dropzone/2009/05/the-free-consultant-iscsi-part-ii.html |
References
- ↑ http://www.heise.de/netze/artikel/Booten-via-Netzwerk-223906.html
- ↑ http://www.etherboot.org
- ↑ http://wpkg.org/Diskless_/_remote_boot_with_Open-iSCSI
- ↑ A “Multivendor Post” to help our mutual iSCSI customers using VMware Question 3: Do I use the Software Initiator or the Hardware Initiator?
- ↑ A “Multivendor Post” to help our mutual iSCSI customers using VMware Quote: "iSCSI target = an iSCSI server, usually on an array of some type. Arrays vary in how they implement this. Some have one (the array itself), some have many, some map them to physical interfaces, some make each LUN an iSCSI target." and Question 1: How do I configure MPIO
- ↑ RFC 3720 Section 3.2. iSCSI Concepts and Functional Overview
- ↑ RFC 3720 Section 3.3 iSCSI Session Types